Replace HP iLO security certificates
When you access the HP iLO webinterface, you will be redirected to a HTTPS website. This connection is usually secured by a self-signed SSL certificate. To replace this certificate with a certificate that was issued by your own CA, you have to complete several steps. I will guide you to the steps. I focused on HP ilO 2, but the steps are similar for iLO 3 or iLO 4.
The requirements
We need:
- an iLO interface that is connected to the network and that has an ip address assigned
- access to this iLO interface
- a CA and access to it
- a web browser
Create the Certificate Signing Request (CSR)
Before we can issue the certificate, we need to create a certificate signing request. This request is used by the CA to create the digital certificate. The CSR contains information to identifying the applicant. This is e.g. the distinguished name (DN), which is the FQDN for a webserver. To create a CSR we have to login into the iLO webinterface.
Create the CSR, issue and install the certificate
I use a Microsoft Windows Server 2012 R2 CA in my lab. This CA is integrated into my Active Directory and I use it to issue certificates for my lab infrastructure. Because it’s my lab, I don’t use a two-tier CA with an offline root CA. ;) But if you are interested in how to setup this, I recommend this two excellent articles written by Derek Seaman and posted on his blog: Windows Server 2012 R2 Two-Tier PKI CA Pt. 1 & Windows Server 2012 R2 Two-Tier PKI CA Pt. 2.
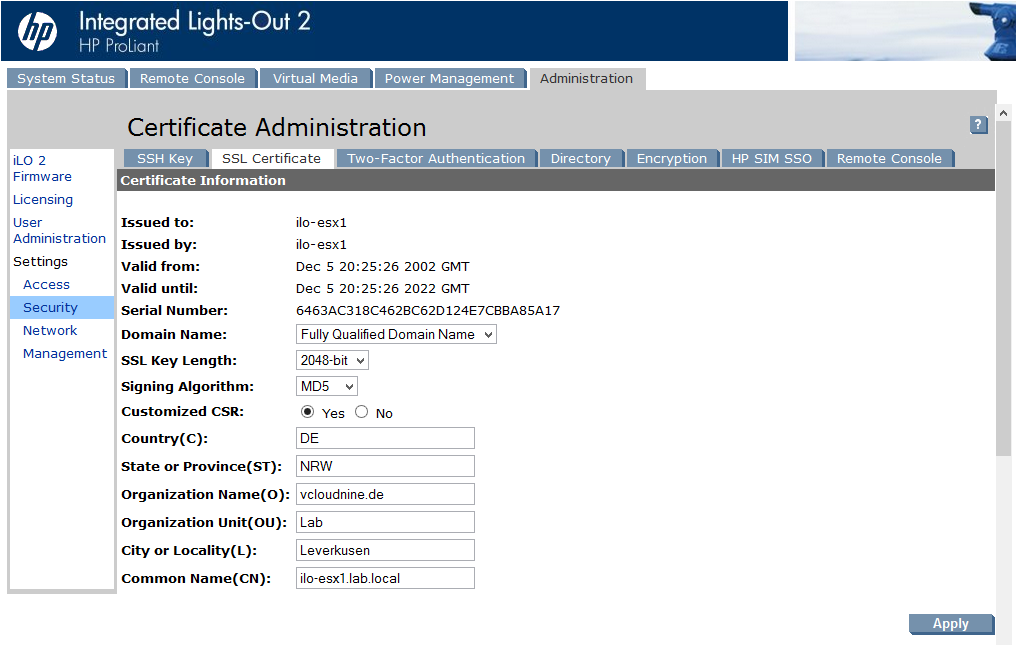
To create a CSR we have to login into iLO and access the “Administration” tab. Then select “Security” from the left menu.
Patrick Terlisten/ vcloudnine.de/ Creative Commons CC0
Usually the lower fields are greyed out, so you have to enable “Customized CSR”. Then you can fill the lower, now enabled fields, with values. Don’t forget to hit apply.
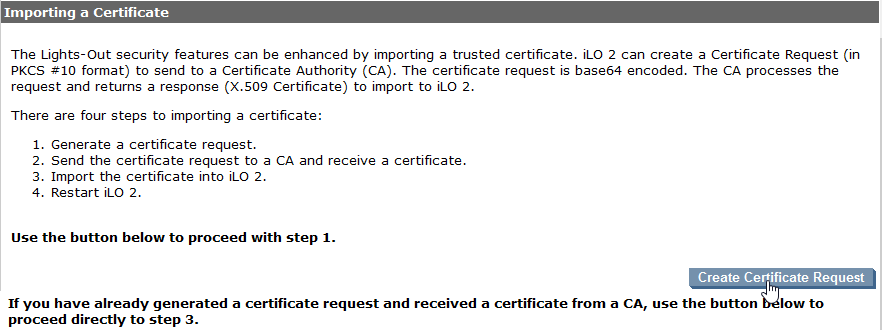
A little further down the page, you can create a certificate request.
Patrick Terlisten/ vcloudnine.de/ Creative Commons CC0
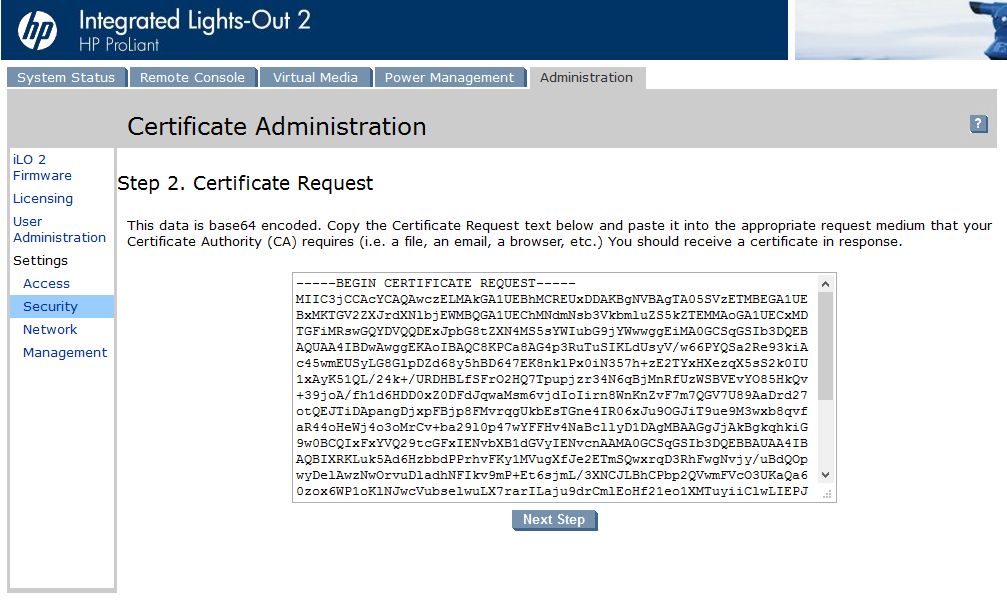
Click the “Create Certificate Request” button. The certificate request will be generated and you will forwarded to the next page. Now you have to copy the request into a text file or you can past it directly into you CA. I use a W2K12 R2 CA which is running on another host. So I copied the text into a file and saved the file as ilo-esx1.csr.
Patrick Terlisten/ vcloudnine.de/ Creative Commons CC0
No it’s time to issue the certificate. I copied the CSR to my CA into a temp directory. Open an elevated CMD, switch to the directory with the CSR and run the following command:
certreq.exe - submit - attrib "CertificateTemplate:WebServer" ilo-esx1.csr ilo-esx1.pem
A windows will pop up where you have to chose the CA. Because I only have on CA, I can’t choose much… Select you CA and click “OK”. Copy the pem file to you client (or whereever you have the browser with the iLO open), click “Next Step” and then paste the content of the pem file into the text field.
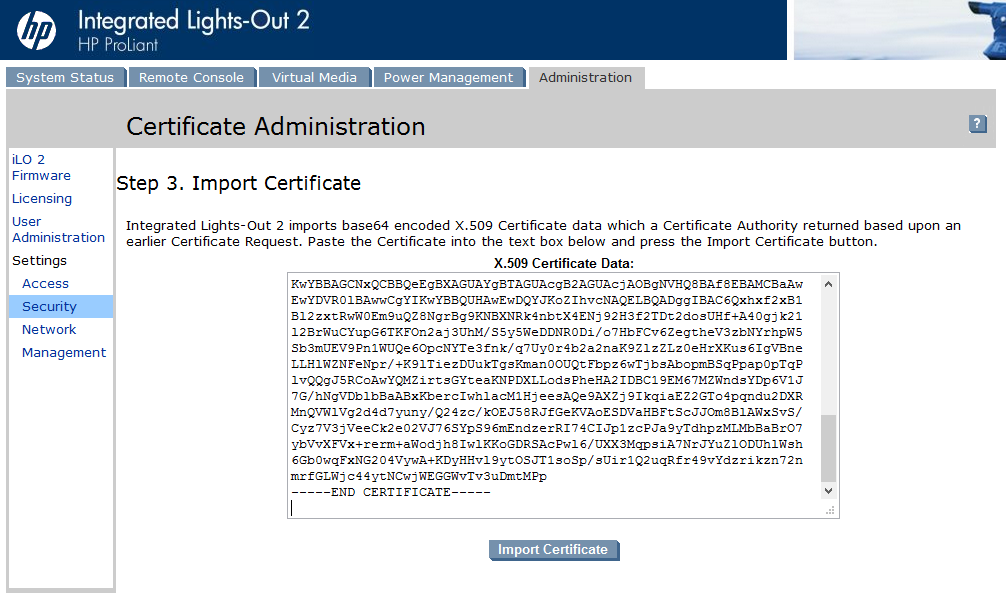
Patrick Terlisten/ vcloudnine.de/ Creative Commons CC0
Click “Install Certificate”.
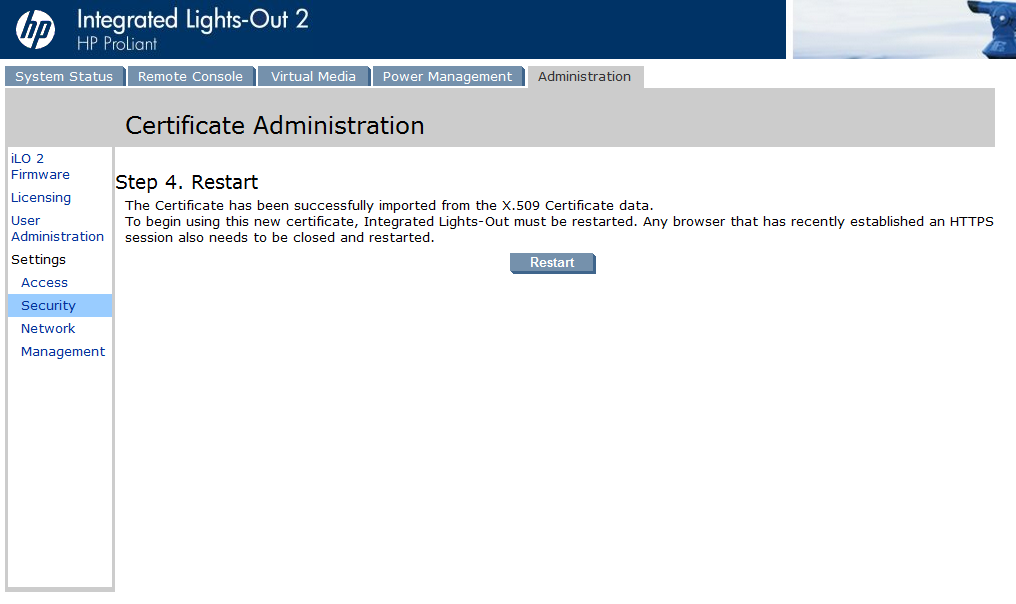
Patrick Terlisten/ vcloudnine.de/ Creative Commons CC0
If you click “Restart” a counter will appear. After 60 seconds you will be redirected to the login page. Please note, that you have to access the login page via the FQDN. Otherwise you will get a certificate error.
Summary
Essentially there is nothing special. It’s much more easier as to do this for a VMware environment… It’s a simple three-step plan: 1. Create the CSR, 2. issue a certificate by using the CSR and 3. install the certificate. Don’t forget to import the CA certificate into you browser. Otherwise you will furthermore get this nasty security warning…
